“Agents versus Agentless” is a very old debate within IT circles. Like many persistent arguments, any given version of it usually ends with “it depends”. It is a pros-and-cons weighing exercise that rests heavily on a number of circumstances.
For those not familiar with the debate, it comes down to one defining question: Do you trust whoever built the agent enough to install it and let it run on your critical infrastructure?
Agent-based monitoring systems require you to install some software onto the device of interest – or compile it into the code of your precious applications. That often puts IT and application managers on edge:
- What if it breaks the server?
- Can you be sure it does not have a memory leak?
- Does it use a lot of the local CPU for its own processing?
- Is it secure? Does it use encrypted communications?
- Do we have to put one on every server?
- How do I choose which servers to put it on?
- How often do patches come out?
- Do they work in virtualized environments as well?
- Will this one conflict with the five other agents I had to install on this server?
Once agents are installed, they can provide an incredible amount of information about the inner workings of a system or device. It is like turning the lights on an otherwise black box. But the view tends to be limited to the local device where it is installed. And the risk, if not the impact, of the installation can make you hesitate.
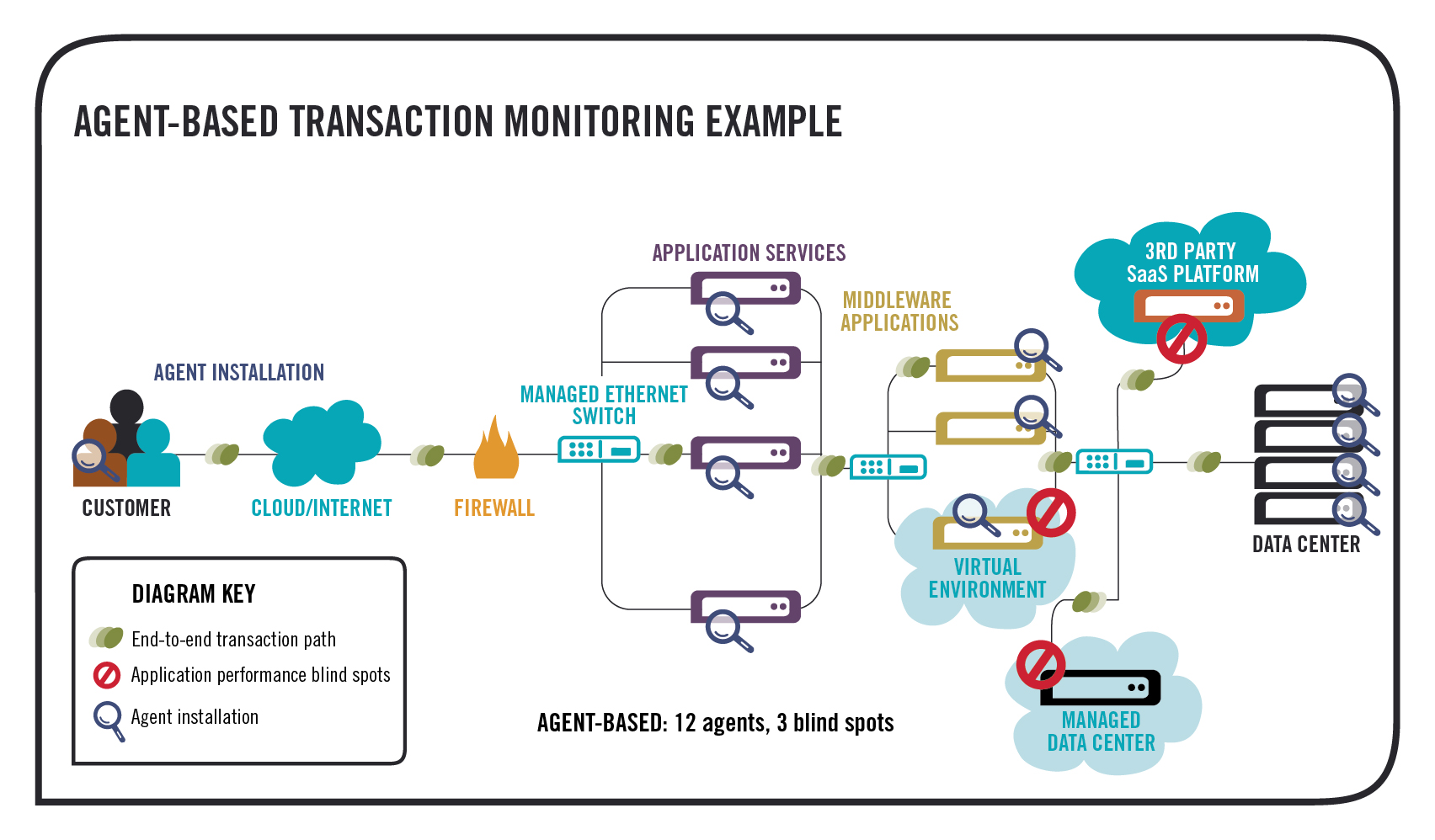
Agentless approaches, on the other hand, have been attractive if only for avoiding all this teeth-gnashing. Agentless monitoring does not require software to be installed on your systems – usually it relies on some existing agent or interface that is part of a device, such as a native service or daemon – or it consumes some “opportunistic” source of data, such as a syslog file. These data sources are usually available or being generated, regardless of monitoring, and can be accessed without major modifications to the critical infrastructure.
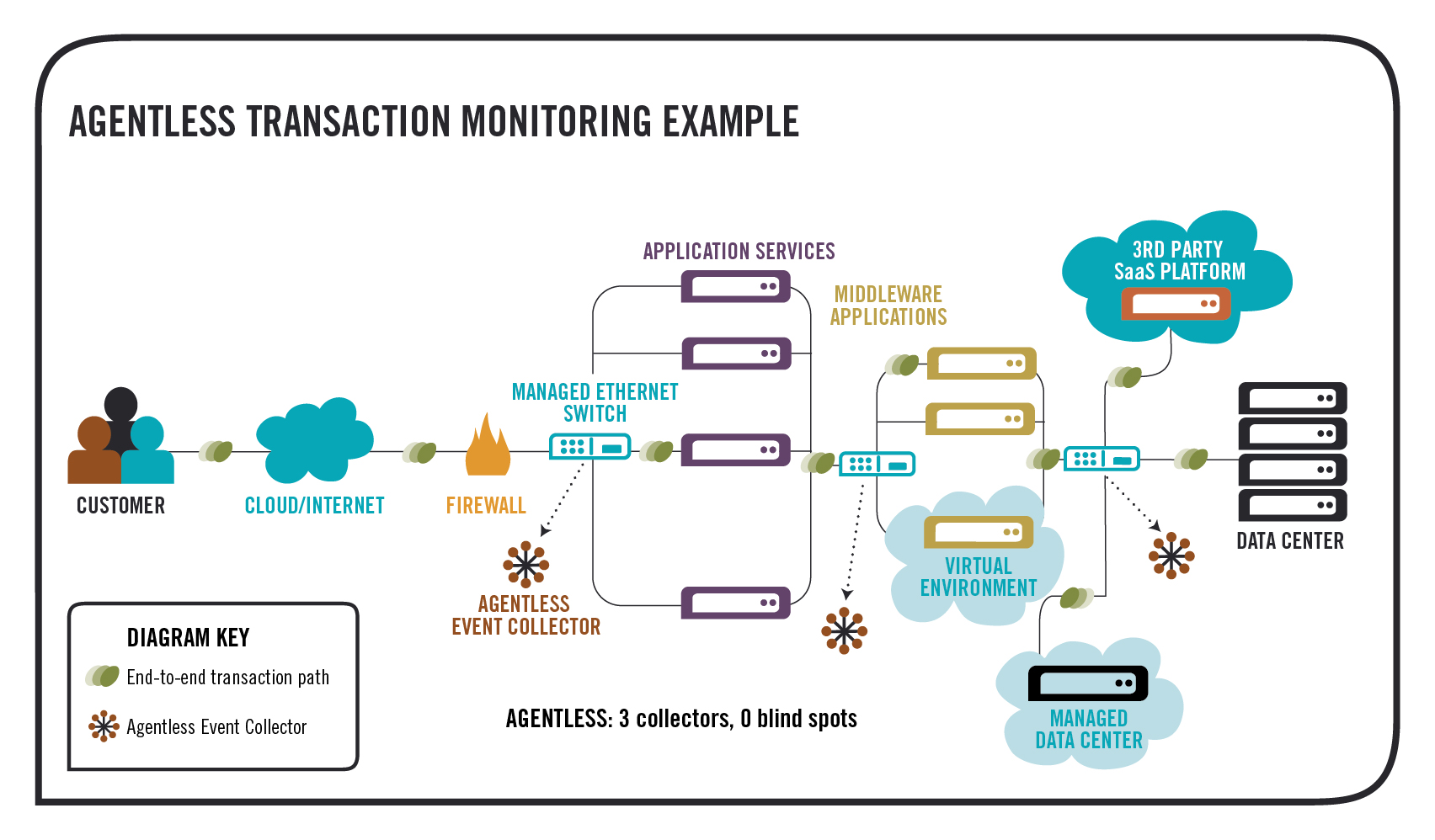
One thing to determine, when considering an opportunistic source of data, is just how rich the information is. It is true these sources are rarely as rich as an agent-based source…But there are notable exceptions. When the opportunistic data source is network traffic, there are a great number of advantages worth noting:
- always on – no additional configuration of the servers required
- a very rich source of data
- carries at least two levels of information – network and application
- easily accessible (e.g. through the SPAN port of a switch)
- data access independent of critical infrastructure
- views across most or all participating devices (depending on network topology)
This is why, when weighing agents versus agentless for business transaction management, favor tilts heavily toward agentless. Agentless for business transaction management (BTM) refers to the solutions that monitor network traffic as their opportunistic data source. Granular transaction data can be gathered without affecting the capacity or performance of critical applications – a feat that can only be achieved with an agentless transaction management solution.
Most of the usual benefits of agents are available to the agentless BTM approach, such as secured communications, automatic updating of monitoring software, and intelligent local processing that optimizes monitoring. The advantages of agentless for BTM become even stronger when you consider monitoring multiple applications, third party services, and virtual or Cloud-based network infrastructure components. Agents do not provide information on the interoperability of multiple service applications. Agents are also hard to place on 3rd party, virtual or Cloud-based systems. The scalability and elasticity of a monitoring system has to match the environments it is monitoring. Otherwise, it rapidly loses value and upkeep effort increases dramatically.
For a deeper understanding of the agent versus agentless debate, download INETCO’s latest whitepaper: Agent vs Agentless: Extending the Debate from Application Performance Management (APM) to Business Transaction Management (BTM) Solutions
You can also watch this YouTube video extracted from “Loki’s Cryptex: Unlocking Transaction Complexity”
[youtube]http://www.youtube.com/watch?v=rk_Mb7XCz8g[/youtube]


 English
English French
French Portuguese
Portuguese Spanish
Spanish