The growing inter-connectedness of digital systems, combined with the alarming ingenuity of financial criminals, has led to a convergence between payment fraud, cybercrime, and AML. As financial transactions increasingly occur online and real-time payments have expanded to over seventy countries, cybercriminals are exploiting these trends by developing sophisticated schemes to target vulnerabilities in digital payment systems. As a result, payment fraud has become more prevalent and more challenging to detect.
A profusion of new tools available on the Dark Web makes it easier than ever for cybercriminals to steal millions through a combination of social engineering, malware, cyberattacks, identity theft, stolen credentials and mule accounts. These attacks expand vectors beyond the traditional payment fraud methods to include cybersecurity breaches and money laundering techniques. For example, a typical attack may include:
1. The theft of a bank employee’s credentials.
2. Malware is installed on the bank’s network.
3. Funds are routed from bank’s account to a third bank in another country.
4. Withdrawals are made through multiple transactions.
5. Millions of dollars are stolen.
The Cost of Fraud is Adding Up
Nearly $1 Billion in APT Cyber-Fraud
This cyber-fraud threat is not a new problem. As far back as 2013 the Carbanak crime group launched sophisticated attacks that showcased the merging threat vectors of cyberattack, payment fraud and money laundering. The organization infiltrated a bank employee’s computer via phishing and infected the video monitoring system with malware. The infiltration enabled them to capture all activities on the screens of personnel handling money transfer systems. The criminals successfully manipulated international e-payment systems to move funds to offshore bank accounts and make withdrawals. In a separate attack, the gang hacked into banks in Kazakhstan and stole over US$ 4 million. They transferred the funds to 250 payment cards that were distributed throughout Europe. The stolen money was then cashed out at ATMs in a dozen countries. By the time the gang was finally caught by Europol in 2018, their thefts had approached US$ 1 billion.
The Carbanak modus operandi is an excellent example of an advanced persistent threat (APT). These threats are notoriously sophisticated, characterized by their stealthy tactics and long-term presence in a network. Unlike ordinary cyber threats focusing on quick gains, APTs are used by patient fraudsters, often lurking undetected in networks for months or even years. They carefully mine valuable data or set the stage for a large-scale, potentially ruinous attack. They get into financial systems by installing malware on a banking system, or using social engineering to secure login credentials, or they buy them on the dark web. Insider fraud or a spear phishing attack can also install malware on the network. It could be as simple as a bad actor leaving a USB device on a table at a workplace with an executable virus on it. Even though we all know better than to plug in a random USB device people, being people, will make mistakes and plug them anyway.
This sort of multi-pronged attack is often orchestrated by a highly-skilled, well-funded criminal organizations or state-sponsored actors. Fraudsters using APTs often have access to significant resources, allowing them to continually innovate their attack strategies.
The primary goal of these sophisticated attacks is to penetrate the network without detection, maintain access over a long period, and siphon off sensitive data related to financial transactions. Their approach is leisurely. Over time they collect data, redirect funds and create fake beneficiaries. Once they infiltrate a network, they establish a strong foothold and employ various techniques to maintain their presence and continually evolve methods to bypass security measures. They don’t initiate actions that could alert cybersecurity teams to their presence until the final attack, when it’s often too late to detect them or to prevent the loss of funds. Removing them, if you can find them at all, can be difficult. When the attack is eventually launched, it can include the theft of customer and financial information, the launching of ransom attacks, making fraudulent transactions and laundering the funds.
$19 Million Stolen in 3 Hours
Another example of a multi-vector cyber-fraud attack occurred at a large bank in Africa. A spear-fishing email inserted malware into the bank’s ATM switch. Transactions then bypassed the host and were automatically approved. The crooks forged the bank’s credit cards and distributed them to over one hundred people in Tokyo, who then used them to withdraw money from 1400 ATMs in retail stores. Social engineering, cyber attack and payment fraud vectors converged to steal US$19 million in just three hours.
Once the criminals are ready to extract the data or cash out, whether that is after a few days or a couple years, fraudsters will often employ a diversion tactic, such as a DDoS attack, then proceed with the main attack while IT and cyber security teams are distracted by the diversionary attack.
The Growing Sophistication of Cyber-Fraud
Technological Advances Fuel Advances in Fraud
Over time, the finance industry has seen the sophistication of attacks continue to increase and there is no reason to expect that this trend will slow down. Early forms of attack were blunt and brute force, so organizations took the mentality of protecting the perimeter. But as attacks have become sophisticated, this approach isn’t sufficient. Today’s threats are advanced, persistent, polymorphic, and evade detection. They span all levels of the OSI stack, in particular at the network and application levels, and they result in ever increasing losses. And new forms of old attacks such as Distributed Denial of Service attacks (DDOS) increasingly driven by bots, with AI that mimics humans and evades detection.
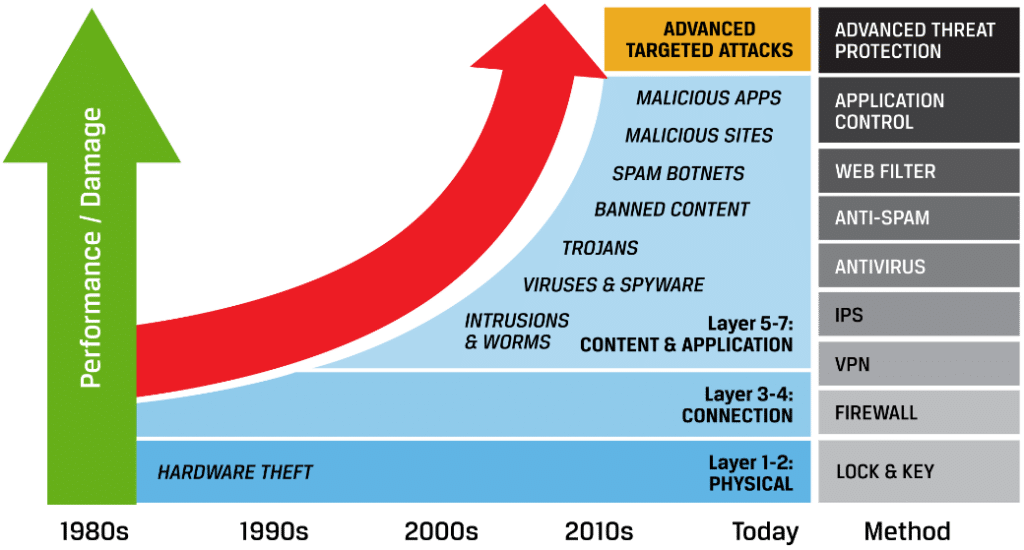
The Evolution of Attacks
Traditionally, AML is about compliance, cybersecurity focuses on preventing IT threats, and fraud programs are for detecting and preventing payment fraud. Within these organizational silos, a card-skimming fraud event would not ordinarily capture the attention of a CISO, while a fraud manager doesn’t make decisions about firewalls.
Traditional Security Methods Fall Short
These traditional organizational silos within companies make tackling this convergence a challenge. Fraudsters exploit the gaps between information security, fraud and risk teams. For example, in an e-commerce setting, a fraudster could run a credential-stuffing campaign using leaked data, take over accounts, check for stored payment information or add a stolen credit card, and purchase expensive luxury items. This type of fraud affects both the retailer and its customers. The fraudster transfers stolen funds to mule accounts, which are often used for money laundering. The fraud and risk team is alerted to the situation through customer complaints or monitoring system alerts. Still, by the time the fraud, cybersecurity, and anti-money laundering (AML) teams have come together to compare notes on the attack, the fraudster has already achieved his objectives and absconded with the funds.
Given the prevalence of these converged threat vectors, the boom in digital transactions and the growth of real-time payments, it should come as no surprise that organizations are starting to leverage the synergies to be had by eliminating organizational silos. The idea of converging cyber intelligence, AML, and fraud prevention activities into cyber-fraud fusion teams in order to eliminate gaps in financial crime risk management have been discussed for years but increasingly, organizations are moving to make this a reality.
Leading financial institutions are establishing robust cyber-fraud fusion teams in financial crimes centers that bring together cybersecurity, anti-fraud and AML resources. These teams converge their data and processes for a more holistic view of the threat landscape. This helps financial institutions identify financial crimes across the spectrum and stay agile in their preventive operations and response.
Implementing a Cyber-Fraud Team
Trends in Fraud Prevention Today
Some large banks have already implemented cyber-fraud fusion centers to identify and defend against financial crimes and ever-evolving threats. For example, Bank of Montreal established a fraud fusion center in January 2019 while TD Bank opened their fusion center in October of the same year. But as criminals introduce new, sophisticated techniques, banks are revamping their fusion centers and looking to improved technology to keep up.
Gartner anticipates an increase in the number of organizations implementing cyber-fraud teams over the next several years. As the initial step in the convergence program, PwC recommends that financial institutions examine their existing enterprise-wide structure and identify points where streamlining it will give senior management a centralized view of financial crime risk. Clearly documented structure with roles and responsibilities will help detect and eliminate duplicate tasks and will ensure better data visibility across cyber-fraud fusion teams.
McKinsey & Company suggests that strategic prevention should be key to improving protection of the bank and its customers when working on convergence. To achieve their goals, financial institutions need to think like the criminals. Cybercriminals are looking for systems’ weak points, so when planning the defense, organizations should trace the flow of crime in order to come up with an optimized internal structure.
Access to the right data at the right time is the foundation of efficient convergence programs. Instead of collecting data and tackling crimes in the silos of compliance, fraud, and cybercrime, data fusion provides a single source of data to multiple teams. This enables a complete view of the payment transactions journey and enables faster, more effective responses to threats.
Criminals don’t make a distinction between AML, fraud or cybercrime departments. They act based on whatever gaps in the system they can find. Information fusion is the best weapon against fraudsters. If cyber-fraud fusion centers leverage raw payment data in real-time, captured at the network level to avoid data loss, they can derive trends and patterns that let them distinguish legitimate customer transactions from fraudulent ones.
Getting Ahead of Evolving Cyber-Criminals
Artificial intelligence and machine learning (ML) also support financial institutions in their privacy compliance by helping prevent data breaches. They can cut through the noise by flagging suspicious activity with precision, blocking fraudulent activities, and letting the legitimate transactions complete.
Faster payments and open banking require organizations to quickly identify and respond to emerging fraud and cyberattack patterns, without creating negative friction for their real customers.
At INETCO, we’ve anticipated these needs and designed INETCO BullzAI, a real-time, ML-powered software solution that address the converged attack vectors of payment fraud, cyberattacks and money-laundering. It provides the real-time data that cyber-fraud fusion teams need and gives them the power to prevent cyber- and fraud attacks while reducing false positives. Get in touch to see how we can help you implement your cyber-fraud prevention strategy.



 English
English French
French Portuguese
Portuguese Spanish
Spanish