Welcome to blog 2 of our 3-part series featuring top recommendations to help financial institutions (FIs) navigate the impact of COVID-19 on their payment business. Last week’s blog shared tips to manage the surge in online and mobile banking transactions. This week, we’ll focus on card-not-present fraud, and how a cyber threat intelligence platform can help.

As we inch closer to June, the coronavirus continues to affect consumer purchasing behaviors – including an immense payments shift towards digital banking and e-commerce. With fraudsters preying on the massive volumes of payment and stimulus transactions occurring around the world, financial institutions are seeing rising numbers of payment fraud, infosecurity and cybersecurity threats. In fact, Google has reported identifying more than 18M daily digital fraud, malware and phishing emails related to COVID-19. Here at INETCO, we can also confirm that we are seeing many of these phishing emails in our spam folders!
To combat evolving risk and security threats associated with COVID-19, financial institutions must revisit whether they are ready to weather this opportune time for a fraud outbreak by installing threat intelligence platforms. INETCO will often work with CISOs, cybersecurity and payment fraud teams to consider how they can:
- Revisit payment fraud and cybersecurity strategies to improve threat intelligence
- Think about card-present and card-not-present visibility across all payment channels. Although there is no silver bullet for everything, real-time transaction-level visibility should be considered a key component of your strategy, especially as threats continue to evolve. Make sure you have the necessary rules and business logic in place for real-time payment fraud detection and prevention. There has never been a better time to adopt a layered defense strategy such as a threat intelligence platform.
- Utilize real-time transaction-level event monitoring
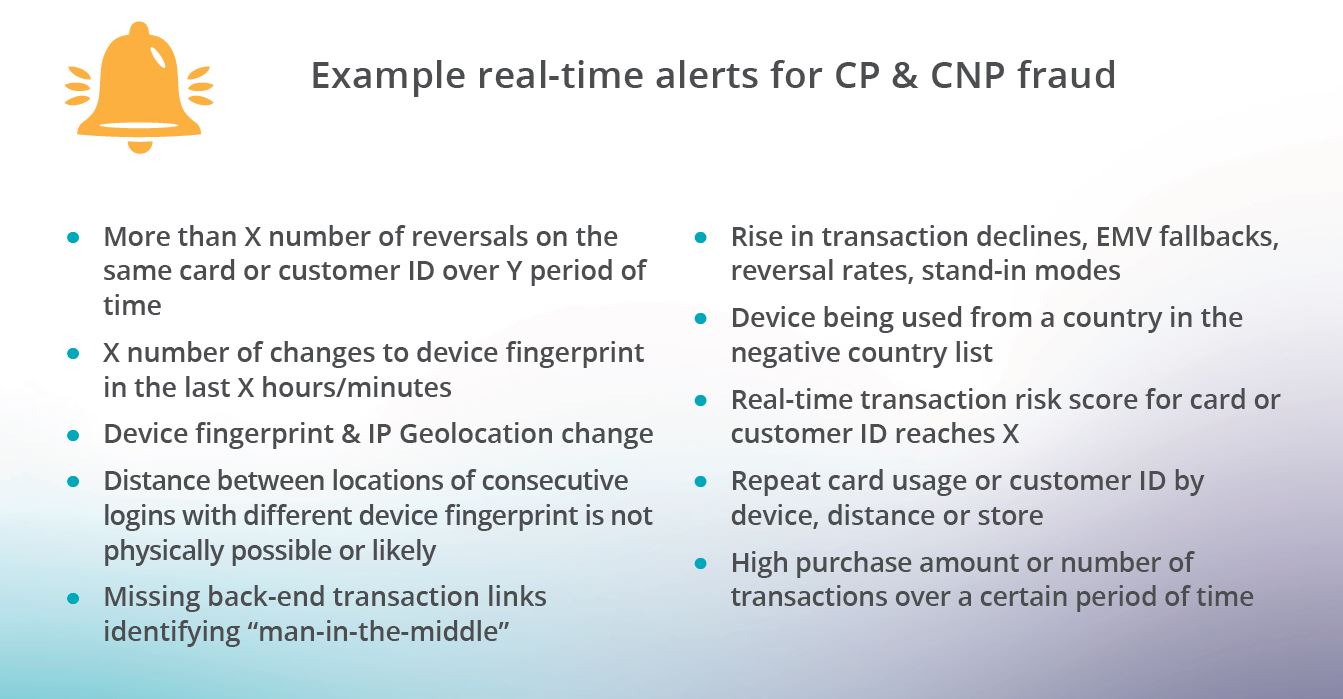
- This is required if you want to immediately increase threat intelligence by detecting various attack patterns aimed at exploiting digital payments and stimulus transactions. These include:
- Suspicious transaction activity patterns and double reversals
- BOT related DDoS attacks – A sudden rise in transactions to a specific service
- Switch malware attacks – Such as man-in-the-middle
- Phishing, illicit money transfers & account takeover scams – High-risk login activity from specific users
- This is required if you want to immediately increase threat intelligence by detecting various attack patterns aimed at exploiting digital payments and stimulus transactions. These include:
- Customize real-time alerts, supervised and unsupervised machine learning
- Make sure you have the flexibility in your threat intelligence platform needed to:
- Configure various transaction rules based suspicious activity
- Look for existing transaction-level fraud patterns in real-time
- Identify new event anomalies (i.e. Surveillance and anomaly reporting for stimulus aid)
- Make sure you have the flexibility in your threat intelligence platform needed to:
- Analyze and adjust risk scoring for the current environment
- Rebuild individual customer models every time a card-present or card-not-present event occurs. Reduce customer friction and false positives through more precise risk scoring that reflects changing usage and payments behaviors
- Block suspicious transactions
- Immediately, and surgically, stop suspicious transaction activity either at the firewall port, IP address or application layer. Take advantage of real-time threat intelligence to quickly investigate these flagged transactions so that you can determine the severity of threat.
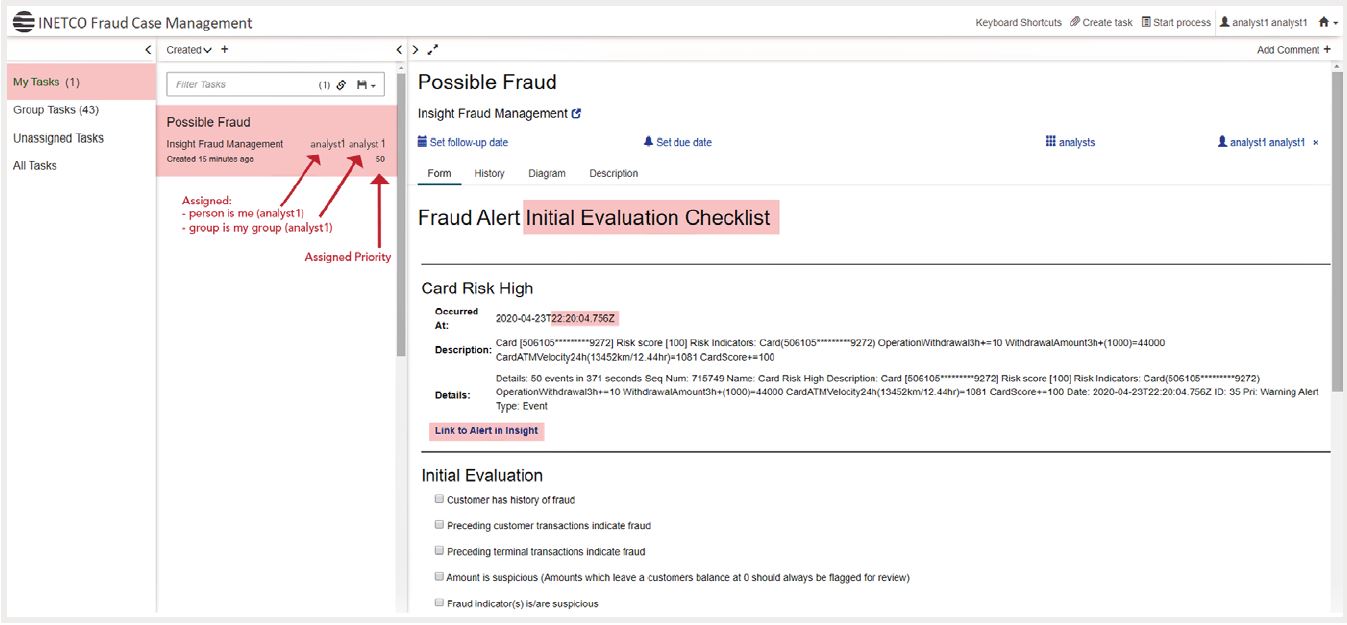
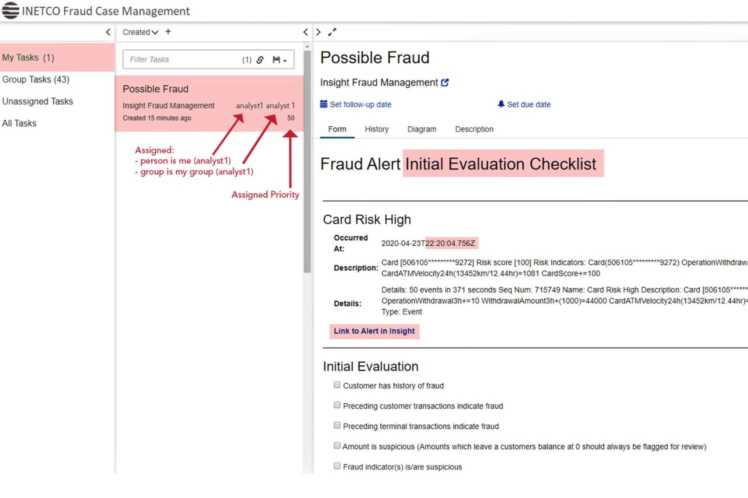
Don’t miss next week’s blog on how to make more impactful decisions around payments revenue and customer service during COVID-19. No patience to wait a week for more tips? Download our whitepaper, Tips to Help Financial Institutions Navigate the Impact of COVID-10 on Their Payments Business, now.
If you are interested in discussing how your financial institution can navigate the impact of COVID-19 while keeping customers happy, send us an email at !