This blog is a part of our new series 5 Strategies for Building Resilience to Financial Crimes and Cyber Attacks in 2022.
In the last few years, we have all observed an increase in the sophistication of cyber-enabled attacks and financial crimes. This coincided with intensified focus on digital banking by financial institutions and increased volumes of online transactions.
Fraudsters and cybercriminals quickly jumped on the opportunity to exploit weak links just when many businesses were at their most vulnerable, trying to adjust to a new, pandemic-driven reality.
Arkose Labs reported in their 2022 State of Fraud & Account Security Report that in 2021, 86% of all attacks were automated attacks (bots) and that the complexity of bot detection increased by three times, as bots were successful in mimicking human behavior with AI.
When planning a crime, bad actors look for gaps in the payment ecosystem. If we adopt a holistic approach and the mindset of criminals, we’ll be able to look at the transaction processes as a whole system and better identify weaknesses and improve enterprises’ fraud prevention strategy. If weaknesses aren’t understood, they can’t be fixed.
Here are three different ways to help you identify weak links in the payment transaction cycle in an enterprise’ fraud prevention strategy:
- Assess if you have the right data. Are you monitoring all areas that should be monitored?
- Check if you are monitoring for the correct threats. Do you have the ability to monitor for both known fraud signatures as well as ‘unknown unknowns’ that have not been seen before?
- Think like a bad actor: where are the coverage gaps from the perspective of a cybercriminal?
Let’s take a close look at each of these questions.
1. Do you have the right data?
To perform the assessment of your defense strategy the right way, Gartner recommends using a layered approach. In their 5 Layers of Fraud Prevention report they advise FIs to monitor and analyze the following areas:
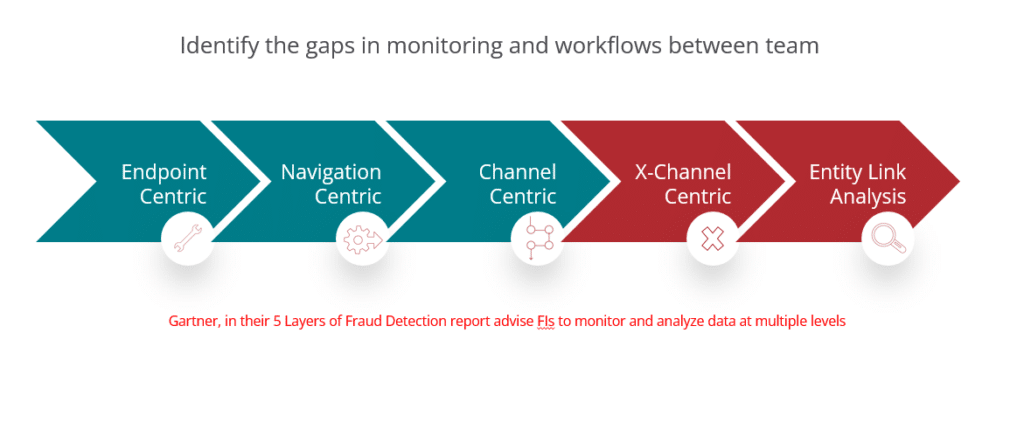
Discrete Analysis:
1. Endpoint centric: This includes the analysis of users and endpoints, including user authentication, and device ID. For example, when you capture failed authentications do you also link this information with other behavior triggers?
2. Navigation centric: This is the analysis of user navigation behavior including IP-addresses and User IDs. Can your system build a customer profile on the fly, analyzing data in real-time? Can your system compare users’ behavior with what is expected of them?
For example, INETCO BullzAI for Payment Fraud Prevention uses sensors to capture traffic directly off the network at various Policy Information Points (PIP) along the transaction journey. Transactions are decrypted and decoded in milliseconds, making every field of every message, as well as timing and duration, available to a central Policy Decision Point (PDP) where the decision on a specific transaction is made. This decision is based on a combination of rules and machine learning, both supervised and unsupervised, which is extensively leveraged to detect anomalies in expected behavior.
3. Channel centric: This is drilling down on user behavior by channel, including details of each transaction and ID proofing at Customer Service Points.
Connected Analysis:
4. Cross-Channel centric: This entails analyzing the totality of all user behavior across all channels with which they interact.
5. And last but not least, Entity Link analysis. This can be used to visualize data to enable better analysis, especially in the context of links, whether Web links or relationship links between people or between different entities.
Most financial institutions have multiple solutions for discrete and connected analysis. At INETCO, we recommend a fusion approach – a convergence of fraud prevention, AML, and cybersecurity efforts to better prevent disruption of your business and improve your resilience to financial crimes and cyber attacks.
As part of adopting a fusion approach FI’s need to understand:
- How good is the data I am getting? Can it be leveraged to detect new attack vectors and threats?
Software with supervised and unsupervised machine learning capabilities is essential here for an in-depth transaction data analysis and spotting anomalies in real-time.
- Is the data readily available to each of the fraud, AML, and cybersecurity teams that need it?
2. Are you monitoring for the correct cyber threats?
Here’s what Gartner recommends as components of a successful payment fraud management strategy:
- Malware detection for your entire infrastructure: from clients and terminals to banking hosts and transaction switches.
- Bot detection across your entire network at both the network and application layers.
- Behavior analysis and biometrics to ensure individuals and entities are authenticated and are who they claim to be.
- Device telemetry and ID to provide a view of the entire digital journey end-to-end, from the client device to the authorization host and back again, including all on-us and off-us data.
- Event monitoring provides visibility into the underlying network behavior associated with transactions.
- And last but not least, Session monitoring to identify unauthorized sessions that can indicate malicious behavior.
For each of these components, it is important to identify the strengths and limitations of your current systems. It’s also valuable to determine what information from each component needs to be available to a fusion team.
As part of this exercise, it is useful to visualize each attack vector. For each point of interaction with your systems, identify if the data and systems you have to detect the attack are adequate to block it before damage is done.
Here is an example of a man-in-the-middle attack. Malware is placed on the transaction switch, enabling the creation of cloned cards which are distributed to money mules. Once the switch is compromised, and the malware is activated, the transaction switch goes into a stand-in mode and starts to approve the fraudulent transactions across a large number of ATMs.
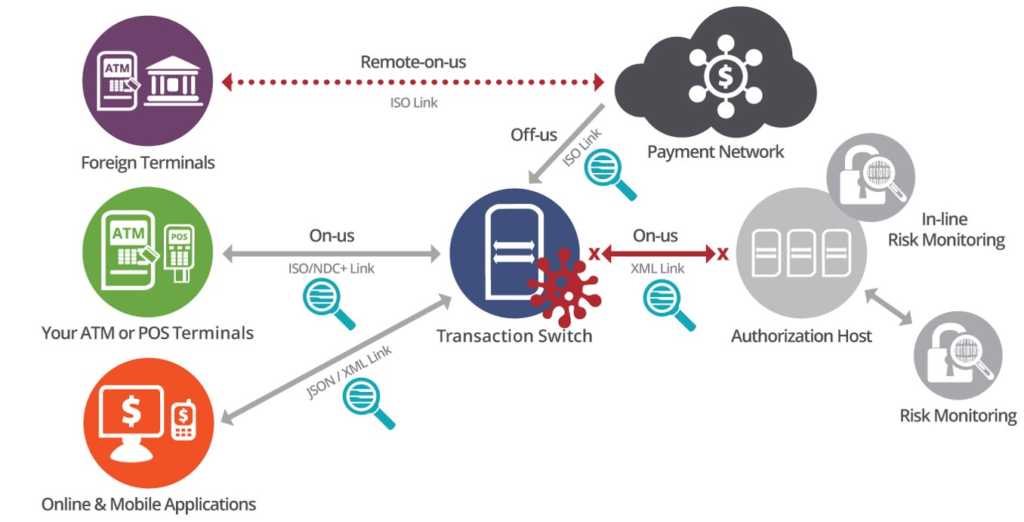
As transactions never go to the back end to be authorized, the limits on accounts are not enforced and fraud detection systems are blind. Criminals can withdraw an unlimited amount of cash without ever being detected or stopped. In the example above, the amounts stolen are in the 10’s of millions of dollars.
| To learn more about preventing man-in-the-middle attacks, read our blog.
3. Think like a bad actor: where are the coverage gaps from the perspective of a cybercriminal?
As we build our payment fraud prevention strategies we often take the perspective of victims, not criminals. It’s like installing a solid lock and a video surveillance system on the front door of your home, but forgetting to check the locks on your windows and back door.
It could be that your weakest link is not authentication, for example, but the quality of the data you are analyzing. Or maybe, it’s risk scoring.
By evaluating regularly the quality of data, threat monitoring, and coverage gaps – you’ll be able to significantly improve your defense against sophisticated financial crimes. As a result, you can expect less disruption to both your business and your customers.
To learn how INETCO can help you strengthen those weak links, book a free consultation with one of our experts.


 English
English French
French Portuguese
Portuguese Spanish
Spanish