
While major, multi-million dollar man-in-the-middle attacks have remained under the radar in recent months, spear phishing and social engineering attacks are on the rise as fraudsters continue to take advantage of the uncertainty surrounding COVID-19.
Spear phishing, social engineering, internal fraud and proxy switches are the preferred weapons of choice used in man-in-the-middle attacks. Through a combination of these tools, malware is introduced into a bank environment anywhere along the transaction journey, often laying dormant for quite some time. In the case of an ATM cash-out scenario, malware is placed on a transaction switch, card information is then used to create cloned cards and distributed to money mules. Successive attacks are then launched from a large number of ATMs.
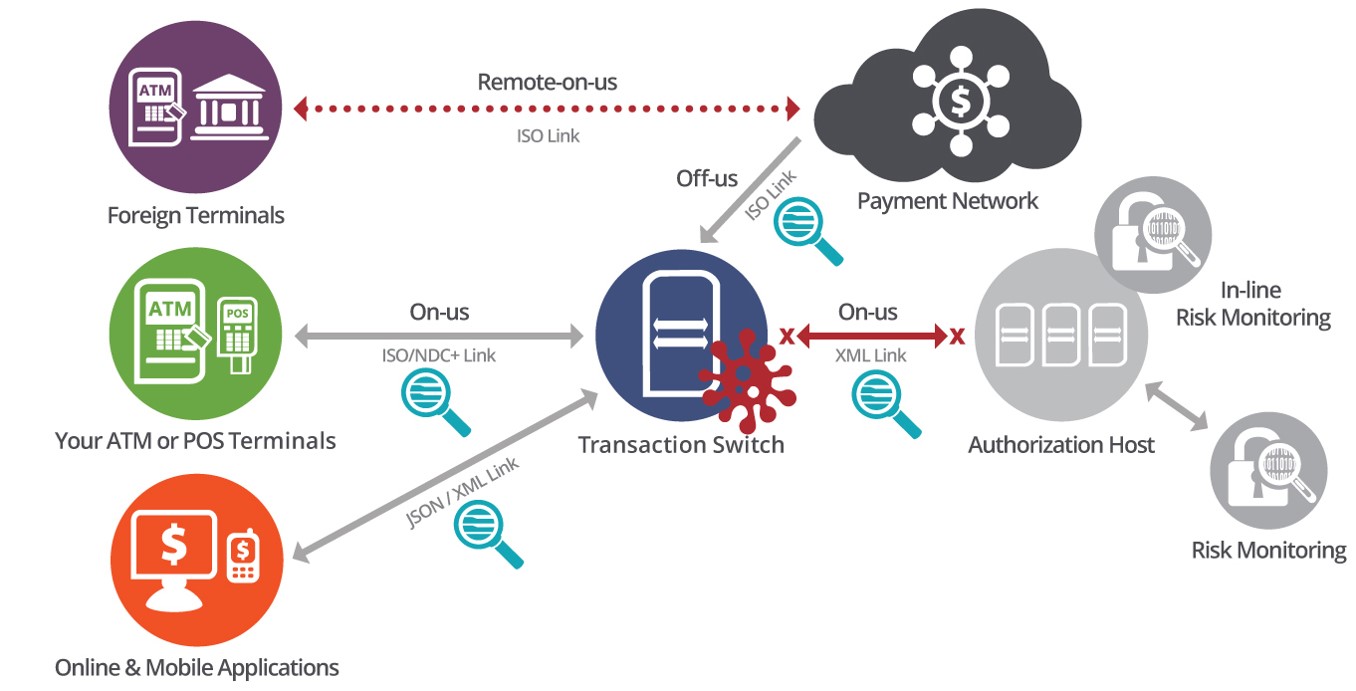
Once the switch is compromised and the malware is activated, the transaction switch goes into a stand-in mode and starts to approve the fraudulent transactions. As transactions never go to the back-end to be authorized, the limits on accounts are not enforced and fraud detection systems are blind sighted. With fraud systems blind, an unlimited amount of attacks and withdrawals can happen without ever being detected or stopped.
Taking a preemptive approach
Taking a preemptive approach towards detecting and preventing man-in-the-middle attacks requires us to start thinking real-time.
By adopting in-depth, real-time network-based transaction monitoring and multi-link correlation capabilities, financial institutions and payment processors can gain a one-stop view into the entire round trip transaction path. Making it easy to audit every end-to-end transaction journey independently of the transaction switch.
Continuously screening for suspicious activity and irregular transaction journeys is key to identifying man-in-the-middle attacks that bypass traditional fraud detection systems. Some examples of real-time alerts used to detect these attacks include:
- Missing back-end transactions and unexpected stand-ins
- X number of international transactions within Y hours
- X number of transactions by international cards in the last Y hours
- X or more bank cards carrying out withdrawals on the same foreign terminal within Y minutes
- X number of consecutive magnetic stripe transactions (instead of chip) from a specific ATM
- High velocity card usage (more transactions than X in Y minutes)
- X consecutive transactions exceeding amount limit
- X number of withdrawals in an ATM segment in off-peak time period
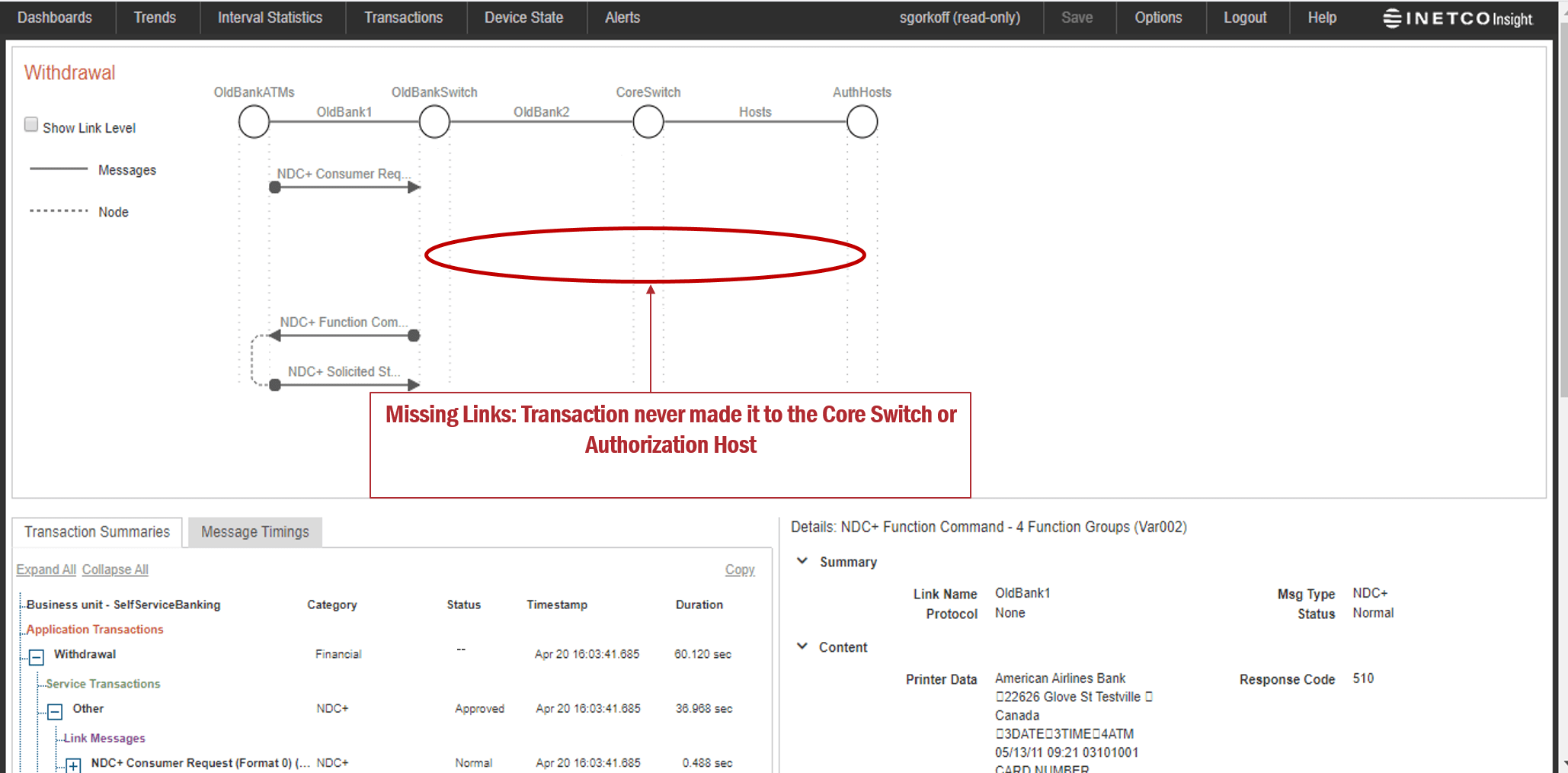
If there has been malware placed on a system that overrides existing fraud controls and is responsible for a man-in-the-middle or an ATM cash-out type of attack, organizations will instantly know when a front-end ISO transaction is not married with a back-end database transaction, or if there have been modified fields in the request/response message.
By adopting a real-time approach to detecting malware, risk advice and action can be assigned in milliseconds, with the option to set up blocking of these transactions at the firewall or application layer. The result is faster detection and prevention, more approved transactions and increased customer trust and safety.
For more ideas on how to protect payment switches from fraud, take five minutes to watch the third video of INETCO’s “1-2-3 Detect Payment Fraud Miniseries”.


 English
English French
French Portuguese
Portuguese Spanish
Spanish